@q3k The first thing I thought when seeing this list of strings was "they directly copied part of the openssh code into the backdoor, and just replaced all strings with encoded strings". For instance, the "mm_" strings can all be found on a normal sshd executable. So my guess is that they divert the flow into their modified copy of the openssh code, instead of doing smaller changes.
|
3 comments
@cesarb I think it might be something like looking for functions which call some symbols, or looking for function calls with debug statements. We're pretty sure somewhere in there is a small x86_64 disassembler :). All of this to be able to patch different versions of openssh. |
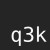
@q3k I just did a quick look at the openssh-portable source code, and many of these strings (including the "xcalloc: zero size" one, which does not make much sense for a backdoor code) can be found there. So my guess is that there's a good chance that a lot of the code you'll find is just the openssh code, the hard part would be to find what has been changed in it.